

You’re looking for information on a particular topic, so you do a web search using your favorite browser. The results page displays the first batch of links, and the first one looks especially promising — from the title and link description, it seems a perfect match. But how safe is that link you’re about to click?
Whether you are using Google, Bing, Yahoo, or another search engine, chances are you trust the results page. Cybercriminals are counting on that. They use automation tools to build fake webpages stuffed with popular search terms (or keywords), tricking search engines into placing those fake sites higher on their results pages. The higher the rank (i.e., the closer to the beginning of the search results), the more likely it is that you’ll click one of those “poisoned” links—and when you do, you’ll open a page that’s loaded with malicious software intended to damage your computer or steal your information.
Getting Clicks at Your Expense
Search engine poisoning isn’t new. “Spamdexing” — a combination of spamming and indexing — became a big issue in the late 1990s as the Internet rose to prominence and people looked to monetize websites by driving traffic to their pages from search engines. Spamdexing is a form of unethical search engine optimization (SEO), a “black hat” technique that deliberately modifies HTML (the standard markup language to create web pages) to include irrelevant or even erroneous information — so spamdexers get clicks at the expense of search engine users. Spamdexing had all but compromised search engines.
And then Google developed a page ranking system that discounted spam sites. Ever since, Google has been updating the algorithms that sniff out and remove black hat sites, and other search engines have followed suit.
Attackers, in return, are constantly updating their methods. Aggressive marketers are working to improve their ranking in search engine results pages artificially. Spammers are looking to make a quick commission based on the number of links clicked, and cybercriminals are hunting easy prey.
A particularly effective form of search poisoning fools Google’s algorithms and presents a completely different search result to unsuspecting users. This technique, called “cloaking,” tells Google’s search engine one thing but shows something completely different to the user. You think you’re clicking a legitimate link displayed on the results page but are instead tricked into downloading malicious content — compromising your system and effectively handing over your personal information to the attacker.
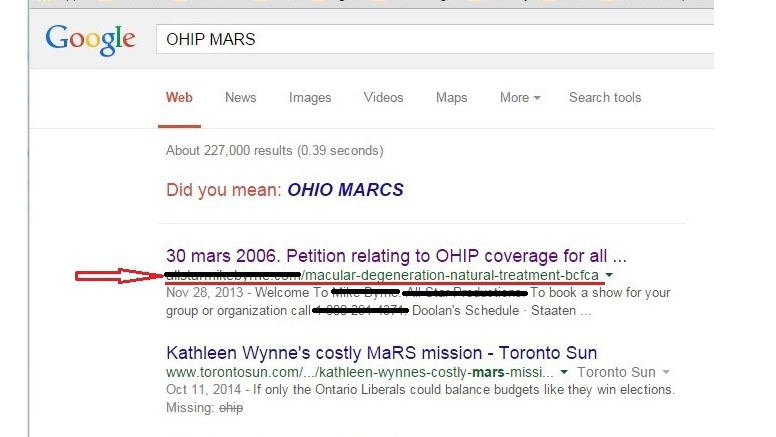
This illustration shows the results of a Google search for a program under the Office of Health Insurance Programs (OHIP). The red arrow points to the first search result, which is labeled as a petition for OHIP, but the URL points to a treatment for macular degeneration.
Poison Control
You can protect yourself from search poisoning and keep both your computer and your personal information safe from attackers. Along with making sure that your browser and antivirus software are up to date, you should follow these key steps:
- Stop and look. When you perform a search through your preferred browser, don’t just click on the first link result. Take a few moments to examine the URLs and the displayed links to make sure they are legitimate.
- Hover. When you hover your cursor over the link — without clicking — you will see the full hyperlinked web address. Check it carefully. If anything looks wrong — misspelled, jumbled, nonsensical — don’t click.
- Check the format. It’s not only fake webpages that can be cloaked — fake PDF links can trick the algorithms and take you to a promoted website or to a page riddled with malware. If you didn’t specifically request a PDF document in your search, don’t click a PDF link.
Remember, all an attacker can do is lead you to poisoned links. No one can make you click.


